Netbus 2 0 Server And Client In Java
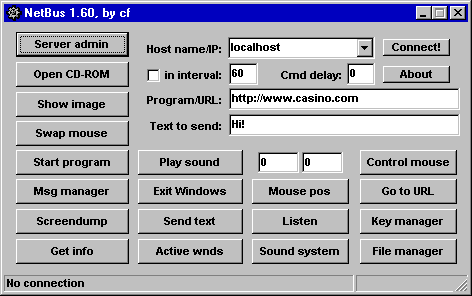
Windows 2000, Windows Server 2003, Windows XP You can download and install SubInACL. Windows 2000. Not every case of a successful intrusion is crowned with a replaced Web site on the server, data theft or damage. Often electronic intruders do not wish to create a. Hidden Backdoors, Trojan Horses and Rootkit Tools in a Windows Environment. Not every case of a successful intrusion is crowned with a replaced Web site on the server, data theft or damage. Often electronic intruders do not wish to create a spectacle but prefer to avoid fame by hiding their presence on compromised systems, sometimes leaving certain unexpected things. They use sophisticated techniques to install specific malware backdoors to let them in again later with full control and in secret. What is malevolent software intended for Obviously, hackers have a variety of motives for installing malevolent software malware. These types of software tend to yield instant access to the system to continuously steal various types of information from it for example, strategic companys designs or numbers of credit cards. MultipleSocketServer1.jpg]];var lpix_1=pix_1.length;var p1_0= [[472' alt='Netbus 2 0 Server And Client In Java' title='Netbus 2 0 Server And Client In Java' />Feature. Description. RESET. Performs a soft configuration reset of the Cisco Model DPC3941B. USB Connector color blue. Optional 2 Each Type 2 USB 2. Muchos me solis pedir recomendaciones sobre qu libros son los ms apropiados para cada uno de vosotros, as que os dejo unas pequeas ideas para que te. In some cases, they use compromised machines as launch points for massive Denial of Service attacks. Perhaps the most common reason hackers tend to settle on another system is the possibility of creating launch pads that attack other computers while disguised as innocent computer addresses. This is a certain kind of spoofing where the intrusion logs fool the target system into believing that it is communicating with another, legitimate computer rather than that of an intruder. Podramos decir que la criptografa es un arte derivado de la ciencia de las matemticas, por eso los criptoanalistas consiguen hacer magia aplicando la disciplina. Under normal conditions, it is hardly to compromise LAN security from the Internet, because in most cases LANs are tied to the Internet via reserved addresses such as type 1. RFC 1. 91. 8 document available at http www. Thus, a hacker cannot have direct access from the Internet, which presents a certain problem for him. Installing shell programs e. Telnet on any Internet accessible computer will allow the intruder to gain access to the LAN and spread his control over the infrastructure. Such types of attacks are prevalent on Unix computers, because they use more common remote access shell services SSH, or more rarely, Telnet and no additional installation is required. This article will, however, focus on Microsoft Windows based systems. Symantec security products include an extensive database of attack signatures. An attack signature is a unique arrangement of information that can be used to identify. In computing, Virtual Network Computing VNC is a graphical desktop sharing system that uses the Remote Frame Buffer protocol RFB to remotely control another computer. Who will become a victim An intelligent hacker will not try to put his program on a server that is monitored and checked regularly. He will secretly, without the knowledge of any legitimate user. Therefore, his attempts to get in will certainly not be through the main domain controller which has its log frequently examined, network traffic monitored and will detect any alterations immediately. Of course, everything depends on the observance of the security policy and as is well known, network administrators are not always scrupulous in performing their work. Nevertheless, a host that plays no key role in the network makes a perfect target for a hacker. Before commencing the selection process, a successful hacker tends to transfer the zone and thereafter identify probable roles of individual hosts within a domain by deducing the knowledge from their names. A poorly secured workstation, isolated from the main network, may ideally be used for hacking purposes because there would be a little chance to detect signs of an installed backdoor. Backdoors. A backdoor is a program or a set of related programs that a hacker installs on the victim computer to allow access to the system at a later time. A backdoors goal is to remove the evidence of initial entry from the systems log. PSC/screenshots/PIC2002412827593163.gif' alt='Netbus 2 0 Server And Client In Java' title='Netbus 2 0 Server And Client In Java' />

 But a nice backdoor will allow a hacker to retain access to a machine it has penetrated even if the intrusion factor has in the meantime been detected by the system administrator. Resetting passwords, changing disk access permissions or fixing original security holes in the hope of remedying the problem may not help. A trivial example of a backdoor is default BIOS, router or switch passwords set either by careless manufacturers or security administrators. A hacker could simply add a new user account with administrator privileges and this would be a sort of backdoor, but far less sophisticated and easy detectable. Adding a new service is the most common technique to disguise backdoors in the Windows operating system. This requires involving tools such as Srvany. Srvinstw. exe that comes with the Resource Kit utility and also with Netcat. The principle of this operation is that the srvany. The latter, in turn, listens on an appropriate port for any connection. Once connected, it will have spawned a remote shell on the server using cmd. Just before commencing the installation of a backdoor, a hacker must investigate within the server to find activated services. He could simply add a new service and give it an inconspicuous name, but he would be better off choosing a service that never gets used and that is either activated manually or even completely disabled. It is sufficient to remove it using the Srvinstw. By doing so, the hacker considerably reduces possibility that the administrator will detect the backdoor during a later inspection. Whenever an event occurs, the system administrator will focus on looking for something odd in the system, leaving all existing services unchecked. From the hacker point of view, it is essential to hide files deeply in system directories to protect them from being detected by the system administrator. In time, a hacker will think of naming the tools to be planted on the server disk. Netcat. exe and Srvany. Hackers understand that backdoor utilities must have names that will not attract any undue attention. They use the same approach when choosing an appropriate port for a backdoor. For example, port 5. The technique presented above is very simple but efficient at the same time. It allows a hacker to get back into the machine with the least amount of visibility within the server logs we are obviously not speaking about situations where extra software is used to monitor traffic and there is an efficient event logging system installed. Moreover, the backdoored service allows the hacker to use higher privileges in most cases as a System account. This may cause some problems for an intruder because, notwithstanding the highest permissions, the System account has no power outside the machine. Under this account, disk mapping or adding user accounts is not possible. Instead, passwords can be changed and privileges may be assigned to existing accounts. With a backdoor that has captured the system administrator account, no such restrictions exist. The only problem that remains is related to the change of user password, because a password update is required to restart the related service. An administrator will undoubtedly start noticing log errors, once care for event logging and monitoring is provided. The example given above describes a backdoor that is the most dangerous one from the victim system point of view, because anyone can connect to it and obtain the highest permissions with no authentication required. It may be any scriptkiddie using a portscanning tool against computers randomly selected from the Internet. Hacker dedicated Web sites give examples of many tools that serve to install backdoors, with the difference that once a connection is established the intruder must login by entering a predefined password. CMD 2, Tini 3, Remote. NC 4 or Win. Shell 5 Fig. Telnet. Fig. 1 Win. Shell program may be used to install certain simple backdoors. I once saw a very interesting script named CGI backdoor 6. I considered this to be interesting because an attacker could execute remote commands on the server via WWW. It was a specifically created totally dynamic. Lista de portas dos protocolos TCP e UDP Wikipdia, a enciclopdia livre. A tabela abaixo indica o status da porta com as seguintes cores e legendas. Oficial se a aplicao e a combinao da porta est no IANA list of port assignments No oficial se a aplicao e a combinao de porta no est na lista de portas do IANA e. Conflito se a porta utilizada usualmente por dois ou mais protocolos. EPI se a porta utilizada como padro interno. Porta. Descrio. Status. TCP,UDPReservada. Fora de Servio. 1TCP,UDPTCPMUX Servio de porta TCP multiplexadorOficial. TCP,UDPRJE Remote Job Entry Entrada de trabalho remotoOficial. TCP,UDPECHO protocol. Oficial. 9TCP,UDPDISCARD protocol. Oficial. 11TCP,UDPSYSTAT protocol. Oficial. 13TCP,UDPDAYTIME protocol. Oficial. 17TCP,UDPQOTD Quote of the Day protocol. Oficial. 18TCP,UDPMessage Send Protocol Protocolo de envio de mensagemOficial. TCP,UDPCHARGEN protocol Character Generator Protocol Protocolo de gerao de caracterOficial. TCPFTP File Transfer protocol Protocolo de transferncia de arquivo data port. Oficial. 21TCPFTP File Transfer protocol Protocolo de transferncia de arquivo control command port. Oficial. 22TCP,UDPSSH Secure Shell Shell seguro Usada para logins seguros, transferncia de arquivos e redirecionamento de porta. Oficial. 23TCP,UDPTelnet protocol Comunicao de texto sem encriptao. Oficial. 25TCP,UDPSMTP Simple Mail Transfer Protocol Protocolo simples de envio de e mail usada para roteamento de e mail entre servidores Atualmente utilizada a porta 5. Comit Gestor da Internet no Brasil CGI. Oficial. 26TCP,UDPRSFTP protocolo similar ao FTPNo oficial. TCP,UDPQMS Magicolor 2 printer. No oficial. 37TCP,UDPTIME protocol Protocolo de TempoOficial. TCP,UDPRoute Access Protocol Protocolo de Acesso ao roteadorOficial. TCP,UDPResource Location Protocol Protocolo de localizao de recursosOficial. TCP,UDPGraphics grficosOficial. TCP,UDPHost Name Server Servidor do Nome do HostOficial. TCP,UDPWINS3No oficialConflito. TCPWHOIS protocolo de consulta de informaes de contato e DNSprotocolOficial. TCP,UDPTACACS Login Host protocolProtocolo de Login no HostOficial. TCP,UDPDNS Sistema de nome de domnioOficial. TCPMTP, Mail Transfer Protocol Protocolo de transferncia de e mail6. UDPBOOTP Boot. Strap Protocol server tambm utilizada por DHCP Protocolo de configurao dinmica do HostOficial. UDPBOOTP client tambm utilizada por DHCPOficial. UDPTFTPTrivial File Transfer Protocol Protocolo de transferncia de arquivo trivialOficial. TCPGopher Protocolo para indexar repositriosOficial. Install License On 5508 Controller there. TCPFinger protocol. Oficial. 80TCPHTTP Hyper. Text Transfer ProtocolProcolo de transferncia de Hiper. Texto usada para transferir pginas WWWOficial. TCPHTTP Alternate Hyper. Text Transfer Protocol Protocolo de transferncia de Hiper. TextoOficial. 81TCPSkype protocol. Oficial. 81TCPTorpark Onion routing ORport. No oficial. 82UDPTorpark Control Port. No oficial. 88TCPKerberos Protocolo de comunicaes individuais seguras e identificadas authenticating agent. Oficial. 10. 1TCPHOSTNAME1. TCPISO TSAP protocol. TCPRemote Telnet Service Servio remoto Telnet1. TCPPOP Post Office Protocol Protocolo de Correio Eletrnico, verso 2. TCPPOP3 Post Office Protocol version 3 Protocolo de Correio Eletrnico, verso 3 usada para recebimento de e mail. Oficial. 11. 1TCP,UDPsun protocol Protocolo da sunOficial. TCPident antigo identificador de servidores, ainda usada em servidores IRC para identificar seus usurios. Oficial. 11. 5TCPSFTP, Simple File Transfer Protocol Protocolo de simples transferncia de arquivo1. TCPUUCP PATH1. 18TCP,UDPSQL Services. Oficial. 11. 9TCPNNTP Network News Transfer Protocol Protocolo de transferncia de notcias na rede usada para recebimento de mensagens de newsgroups. Oficial. 12. 3UDPNTP Network Time Protocol Protocolo de tempo na rede usada para sincronizao de horrio. Oficial. 13. 5TCP,UDPEPMAP End Point Mapper Microsoft RPC Locator Service Microsoft RPC Servio de localizaoOficial. TCP,UDPNet. BIOS Net. BIOS Name Service. Oficial. 13. 8TCP,UDPNet. BIOS Net. BIOS Datagram Service Servio de datagrama Net. BiosOficial. 13. TCP,UDPNet. BIOS Net. BIOS Session Service Servio de sesso Net. BiosOficial. 14. TCP,UDPIMAP4 Internet Message Access Protocol 4 Protocolo de Acesso a mensagens na Internet usada para recebimento de e mail. Oficial. 15. 2TCP,UDPBFTP, Background File Transfer Program Protocolo de transferncia de arquivo em Backgroundfundo1. TCP,UDPSGMP, Simple Gateway Monitoring Protocol Protocolo de simples monitoramento do gateway1. TCP,UDPSQL Service Servio SQLOficial. TCP,UDPDMSP, Distributed Mail Service Protocol Protocolo de servio de e mail distribudo1. TCP,UDPSNMP Simple Network Management Protocol Protocolo simples de gerenciamento de redeOficial. TCP,UDPSNMPTRAPOficial. TCPPrint srv Print Server1. TCPBGP Border Gateway ProtocolProtocolo de limite do gatewayOficial. TCPIRC Internet Relay ChatOficial. TCP,UDPApple. Talk Routing Maintenance. TCP,UDPThe Quick Mail Transfer Protocol Protocolo de rpida transferncia de mail2. TCP,UDPIPX Internetwork Packet Exchange Troca de pacote na rea de trabalho da internetOficial. TCP,UDPMPP, Message Posting Protocol Protocolo de postagem de mensagem2. Wibu Crack. TCP,UDPIMAP, Interactive Mail Access Protocol, version 3 Protocolo de acesso interativo ao mail2. TCP,UDPESRO, Efficient Short Remote Operations Operaes remotas de curta eficincia2. TCP,UDPBGMP, Border Gateway Multicast Protocol. TCPApple Server Admin Tool, Workgroup Manager Tool, Ferramenta de gerenciamento de workgroup3. TCP,UDPTSP, Time Stamp Protocol. TCP,UDPIMMP, Internet Message Mapping Protocol Protocolo de mapeamento de mensagem da internet3. TCP,UDPHP Open. View HTTPs Operations Agent. TCP,UDPSMTP, Simple Mail Transfer Protocol Protocolo de simples transferncia de mail. ODMR, On Demand Mail Relay. TCP,UDPRpc. 2portmap. Oficial. 37. 1TCP,UDPClear. Case albd. Oficial. TCP,UDPA Remote Network Server System Sistema servidor de rede remota3. TCP,UDPAURP, Apple. Talk Update based Routing Protocol. TCP,UDPLDAP Lightweight Directory Access ProtocolProtocolo de acesso a diretrio lightweightOficial. TCP,UDPUPS Uninterruptible Power Supply Suprimento de potncia IninterruptvelOficial. TCPDirect Connect Rede de conexo direta, Conexo direta Hub port. No oficial. 41. TCPDirect Connect Client To Client port. No oficial. 42. TCP,UDPSLP Service Location Protocol Protocolo de servio de localizaoNo oficial. TCPHTTPS HTTP Protocol over TLSSSL transmisso seguraCamada de transporte seguroOficial. TCP,UDPSNPP, Simple Network Paging Protocol Protocolo simples de paging de rede4. TCPMicrosoft DS Active Directory, Windows shares, Sasser vrus, Agobot, Zobotworm. Oficial. 44. 5UDPMicrosoft DS SMB Bloco de mensagem de servidor file sharing. Oficial. 46. 4TCP,UDPKerberos ChangeSet password. Oficial. 46. 5TCPSMTP over SSL Conflito registrado com protocolo Cisco. Conflito. 50. 0TCP,UDPISAKMP, IKE Internet Key Exchange. Oficial. 50. 2TCP,UDPModbus, Protocol. TCPexec, Remote Process Execution Processo de execuo remota5. UDPcomsat, together with biff notifica usurios acerca de novos e mails no lidos. TCPLogin. 51. 3UDPWho.
But a nice backdoor will allow a hacker to retain access to a machine it has penetrated even if the intrusion factor has in the meantime been detected by the system administrator. Resetting passwords, changing disk access permissions or fixing original security holes in the hope of remedying the problem may not help. A trivial example of a backdoor is default BIOS, router or switch passwords set either by careless manufacturers or security administrators. A hacker could simply add a new user account with administrator privileges and this would be a sort of backdoor, but far less sophisticated and easy detectable. Adding a new service is the most common technique to disguise backdoors in the Windows operating system. This requires involving tools such as Srvany. Srvinstw. exe that comes with the Resource Kit utility and also with Netcat. The principle of this operation is that the srvany. The latter, in turn, listens on an appropriate port for any connection. Once connected, it will have spawned a remote shell on the server using cmd. Just before commencing the installation of a backdoor, a hacker must investigate within the server to find activated services. He could simply add a new service and give it an inconspicuous name, but he would be better off choosing a service that never gets used and that is either activated manually or even completely disabled. It is sufficient to remove it using the Srvinstw. By doing so, the hacker considerably reduces possibility that the administrator will detect the backdoor during a later inspection. Whenever an event occurs, the system administrator will focus on looking for something odd in the system, leaving all existing services unchecked. From the hacker point of view, it is essential to hide files deeply in system directories to protect them from being detected by the system administrator. In time, a hacker will think of naming the tools to be planted on the server disk. Netcat. exe and Srvany. Hackers understand that backdoor utilities must have names that will not attract any undue attention. They use the same approach when choosing an appropriate port for a backdoor. For example, port 5. The technique presented above is very simple but efficient at the same time. It allows a hacker to get back into the machine with the least amount of visibility within the server logs we are obviously not speaking about situations where extra software is used to monitor traffic and there is an efficient event logging system installed. Moreover, the backdoored service allows the hacker to use higher privileges in most cases as a System account. This may cause some problems for an intruder because, notwithstanding the highest permissions, the System account has no power outside the machine. Under this account, disk mapping or adding user accounts is not possible. Instead, passwords can be changed and privileges may be assigned to existing accounts. With a backdoor that has captured the system administrator account, no such restrictions exist. The only problem that remains is related to the change of user password, because a password update is required to restart the related service. An administrator will undoubtedly start noticing log errors, once care for event logging and monitoring is provided. The example given above describes a backdoor that is the most dangerous one from the victim system point of view, because anyone can connect to it and obtain the highest permissions with no authentication required. It may be any scriptkiddie using a portscanning tool against computers randomly selected from the Internet. Hacker dedicated Web sites give examples of many tools that serve to install backdoors, with the difference that once a connection is established the intruder must login by entering a predefined password. CMD 2, Tini 3, Remote. NC 4 or Win. Shell 5 Fig. Telnet. Fig. 1 Win. Shell program may be used to install certain simple backdoors. I once saw a very interesting script named CGI backdoor 6. I considered this to be interesting because an attacker could execute remote commands on the server via WWW. It was a specifically created totally dynamic. Lista de portas dos protocolos TCP e UDP Wikipdia, a enciclopdia livre. A tabela abaixo indica o status da porta com as seguintes cores e legendas. Oficial se a aplicao e a combinao da porta est no IANA list of port assignments No oficial se a aplicao e a combinao de porta no est na lista de portas do IANA e. Conflito se a porta utilizada usualmente por dois ou mais protocolos. EPI se a porta utilizada como padro interno. Porta. Descrio. Status. TCP,UDPReservada. Fora de Servio. 1TCP,UDPTCPMUX Servio de porta TCP multiplexadorOficial. TCP,UDPRJE Remote Job Entry Entrada de trabalho remotoOficial. TCP,UDPECHO protocol. Oficial. 9TCP,UDPDISCARD protocol. Oficial. 11TCP,UDPSYSTAT protocol. Oficial. 13TCP,UDPDAYTIME protocol. Oficial. 17TCP,UDPQOTD Quote of the Day protocol. Oficial. 18TCP,UDPMessage Send Protocol Protocolo de envio de mensagemOficial. TCP,UDPCHARGEN protocol Character Generator Protocol Protocolo de gerao de caracterOficial. TCPFTP File Transfer protocol Protocolo de transferncia de arquivo data port. Oficial. 21TCPFTP File Transfer protocol Protocolo de transferncia de arquivo control command port. Oficial. 22TCP,UDPSSH Secure Shell Shell seguro Usada para logins seguros, transferncia de arquivos e redirecionamento de porta. Oficial. 23TCP,UDPTelnet protocol Comunicao de texto sem encriptao. Oficial. 25TCP,UDPSMTP Simple Mail Transfer Protocol Protocolo simples de envio de e mail usada para roteamento de e mail entre servidores Atualmente utilizada a porta 5. Comit Gestor da Internet no Brasil CGI. Oficial. 26TCP,UDPRSFTP protocolo similar ao FTPNo oficial. TCP,UDPQMS Magicolor 2 printer. No oficial. 37TCP,UDPTIME protocol Protocolo de TempoOficial. TCP,UDPRoute Access Protocol Protocolo de Acesso ao roteadorOficial. TCP,UDPResource Location Protocol Protocolo de localizao de recursosOficial. TCP,UDPGraphics grficosOficial. TCP,UDPHost Name Server Servidor do Nome do HostOficial. TCP,UDPWINS3No oficialConflito. TCPWHOIS protocolo de consulta de informaes de contato e DNSprotocolOficial. TCP,UDPTACACS Login Host protocolProtocolo de Login no HostOficial. TCP,UDPDNS Sistema de nome de domnioOficial. TCPMTP, Mail Transfer Protocol Protocolo de transferncia de e mail6. UDPBOOTP Boot. Strap Protocol server tambm utilizada por DHCP Protocolo de configurao dinmica do HostOficial. UDPBOOTP client tambm utilizada por DHCPOficial. UDPTFTPTrivial File Transfer Protocol Protocolo de transferncia de arquivo trivialOficial. TCPGopher Protocolo para indexar repositriosOficial. Install License On 5508 Controller there. TCPFinger protocol. Oficial. 80TCPHTTP Hyper. Text Transfer ProtocolProcolo de transferncia de Hiper. Texto usada para transferir pginas WWWOficial. TCPHTTP Alternate Hyper. Text Transfer Protocol Protocolo de transferncia de Hiper. TextoOficial. 81TCPSkype protocol. Oficial. 81TCPTorpark Onion routing ORport. No oficial. 82UDPTorpark Control Port. No oficial. 88TCPKerberos Protocolo de comunicaes individuais seguras e identificadas authenticating agent. Oficial. 10. 1TCPHOSTNAME1. TCPISO TSAP protocol. TCPRemote Telnet Service Servio remoto Telnet1. TCPPOP Post Office Protocol Protocolo de Correio Eletrnico, verso 2. TCPPOP3 Post Office Protocol version 3 Protocolo de Correio Eletrnico, verso 3 usada para recebimento de e mail. Oficial. 11. 1TCP,UDPsun protocol Protocolo da sunOficial. TCPident antigo identificador de servidores, ainda usada em servidores IRC para identificar seus usurios. Oficial. 11. 5TCPSFTP, Simple File Transfer Protocol Protocolo de simples transferncia de arquivo1. TCPUUCP PATH1. 18TCP,UDPSQL Services. Oficial. 11. 9TCPNNTP Network News Transfer Protocol Protocolo de transferncia de notcias na rede usada para recebimento de mensagens de newsgroups. Oficial. 12. 3UDPNTP Network Time Protocol Protocolo de tempo na rede usada para sincronizao de horrio. Oficial. 13. 5TCP,UDPEPMAP End Point Mapper Microsoft RPC Locator Service Microsoft RPC Servio de localizaoOficial. TCP,UDPNet. BIOS Net. BIOS Name Service. Oficial. 13. 8TCP,UDPNet. BIOS Net. BIOS Datagram Service Servio de datagrama Net. BiosOficial. 13. TCP,UDPNet. BIOS Net. BIOS Session Service Servio de sesso Net. BiosOficial. 14. TCP,UDPIMAP4 Internet Message Access Protocol 4 Protocolo de Acesso a mensagens na Internet usada para recebimento de e mail. Oficial. 15. 2TCP,UDPBFTP, Background File Transfer Program Protocolo de transferncia de arquivo em Backgroundfundo1. TCP,UDPSGMP, Simple Gateway Monitoring Protocol Protocolo de simples monitoramento do gateway1. TCP,UDPSQL Service Servio SQLOficial. TCP,UDPDMSP, Distributed Mail Service Protocol Protocolo de servio de e mail distribudo1. TCP,UDPSNMP Simple Network Management Protocol Protocolo simples de gerenciamento de redeOficial. TCP,UDPSNMPTRAPOficial. TCPPrint srv Print Server1. TCPBGP Border Gateway ProtocolProtocolo de limite do gatewayOficial. TCPIRC Internet Relay ChatOficial. TCP,UDPApple. Talk Routing Maintenance. TCP,UDPThe Quick Mail Transfer Protocol Protocolo de rpida transferncia de mail2. TCP,UDPIPX Internetwork Packet Exchange Troca de pacote na rea de trabalho da internetOficial. TCP,UDPMPP, Message Posting Protocol Protocolo de postagem de mensagem2. Wibu Crack. TCP,UDPIMAP, Interactive Mail Access Protocol, version 3 Protocolo de acesso interativo ao mail2. TCP,UDPESRO, Efficient Short Remote Operations Operaes remotas de curta eficincia2. TCP,UDPBGMP, Border Gateway Multicast Protocol. TCPApple Server Admin Tool, Workgroup Manager Tool, Ferramenta de gerenciamento de workgroup3. TCP,UDPTSP, Time Stamp Protocol. TCP,UDPIMMP, Internet Message Mapping Protocol Protocolo de mapeamento de mensagem da internet3. TCP,UDPHP Open. View HTTPs Operations Agent. TCP,UDPSMTP, Simple Mail Transfer Protocol Protocolo de simples transferncia de mail. ODMR, On Demand Mail Relay. TCP,UDPRpc. 2portmap. Oficial. 37. 1TCP,UDPClear. Case albd. Oficial. TCP,UDPA Remote Network Server System Sistema servidor de rede remota3. TCP,UDPAURP, Apple. Talk Update based Routing Protocol. TCP,UDPLDAP Lightweight Directory Access ProtocolProtocolo de acesso a diretrio lightweightOficial. TCP,UDPUPS Uninterruptible Power Supply Suprimento de potncia IninterruptvelOficial. TCPDirect Connect Rede de conexo direta, Conexo direta Hub port. No oficial. 41. TCPDirect Connect Client To Client port. No oficial. 42. TCP,UDPSLP Service Location Protocol Protocolo de servio de localizaoNo oficial. TCPHTTPS HTTP Protocol over TLSSSL transmisso seguraCamada de transporte seguroOficial. TCP,UDPSNPP, Simple Network Paging Protocol Protocolo simples de paging de rede4. TCPMicrosoft DS Active Directory, Windows shares, Sasser vrus, Agobot, Zobotworm. Oficial. 44. 5UDPMicrosoft DS SMB Bloco de mensagem de servidor file sharing. Oficial. 46. 4TCP,UDPKerberos ChangeSet password. Oficial. 46. 5TCPSMTP over SSL Conflito registrado com protocolo Cisco. Conflito. 50. 0TCP,UDPISAKMP, IKE Internet Key Exchange. Oficial. 50. 2TCP,UDPModbus, Protocol. TCPexec, Remote Process Execution Processo de execuo remota5. UDPcomsat, together with biff notifica usurios acerca de novos e mails no lidos. TCPLogin. 51. 3UDPWho.